- Cookie 5 7 5 – Protect Your Online Privacy Screen
- Cookie 5 7 5 – Protect Your Online Privacy Screen Protector
The Internet allows us to download, share, and re-use copyrighted material in many ways. But kids don't always follow the rules. Find out how to educate your kids about both the legal and ethical reasons for respecting other people's creative work. One technology that facilitates web storage is HTML 5. A cookie is a small file containing a string of characters that is sent to your computer when you visit a website. When you visit the site again, the cookie allows that site to recognize your browser. Cookies may store user preferences and other information.
Last modified: February 17, 2019
Most internet users have heard of the concept of 'cookies' that store information about websites they've visited. On the other hand, many people don't realize the scope of information that these cookies capture and how they can be used to monitor your behavior. In recent years, the usage and complexity of browser cookies has increased significantly. This largely went unnoticed by most users. To be sure, minimize this invasive monitoring by reading on. In this post we'll summarize how Cookies gather information about you. Learn how to manage web cookies to protect your online privacy.
What is the Purpose of Browser Cookies?
Cookies are a tool website owners use to track your behavior on their site. They store this information about you for future visits. Information contained in these cookies could e.g. include:
- your IP address,
- browser version information,
- user ID assigned by the site owner,
- the dates you visited the site,
- what pages you viewed or
- which actions you took on the site.
They combine this information into an unique profile assigned to you. Cookies usually don't contain any personal information about you, e.g. your name or phone number. Instead, marketers use these hardware details and build a 'profile' on you they can study and analyze.
One of the most common examples of cookie monitoring is 'retargeting' advertising. In short, a business will continue advertising to you long after you've left their website. Ever notice how you've visited a site and then something from that website (or closely related to it) starts showing up in your Facebook ads? Facebook partners with a massive number of web service providers. They allow them to continue advertising to you on social media after you visit their website. This is just one example – most social media platforms and large websites employ this method of advertising.
How to Manage Web Cookies
Copyclip 2 9 6 download free. This invasive tracking should be concerning to privacy-minded users. The most effective way to prevent cookie usage on your PC is to simply turn them off. But note that this may break some functionality of certain websites.
An acceptable compromise may be to enable cookie deletion upon closing the browsing session – most modern browsers have this ability. You can take this a step further and use the various private-browsing modes available on your browser.
Learn hear how to use:
- Incognito mode in Chrome
- Private mode in Firefox
In short, prevent cookies by using these modes. These modes delete the activities you perform during these session. They also delete any temporary files created during the session.
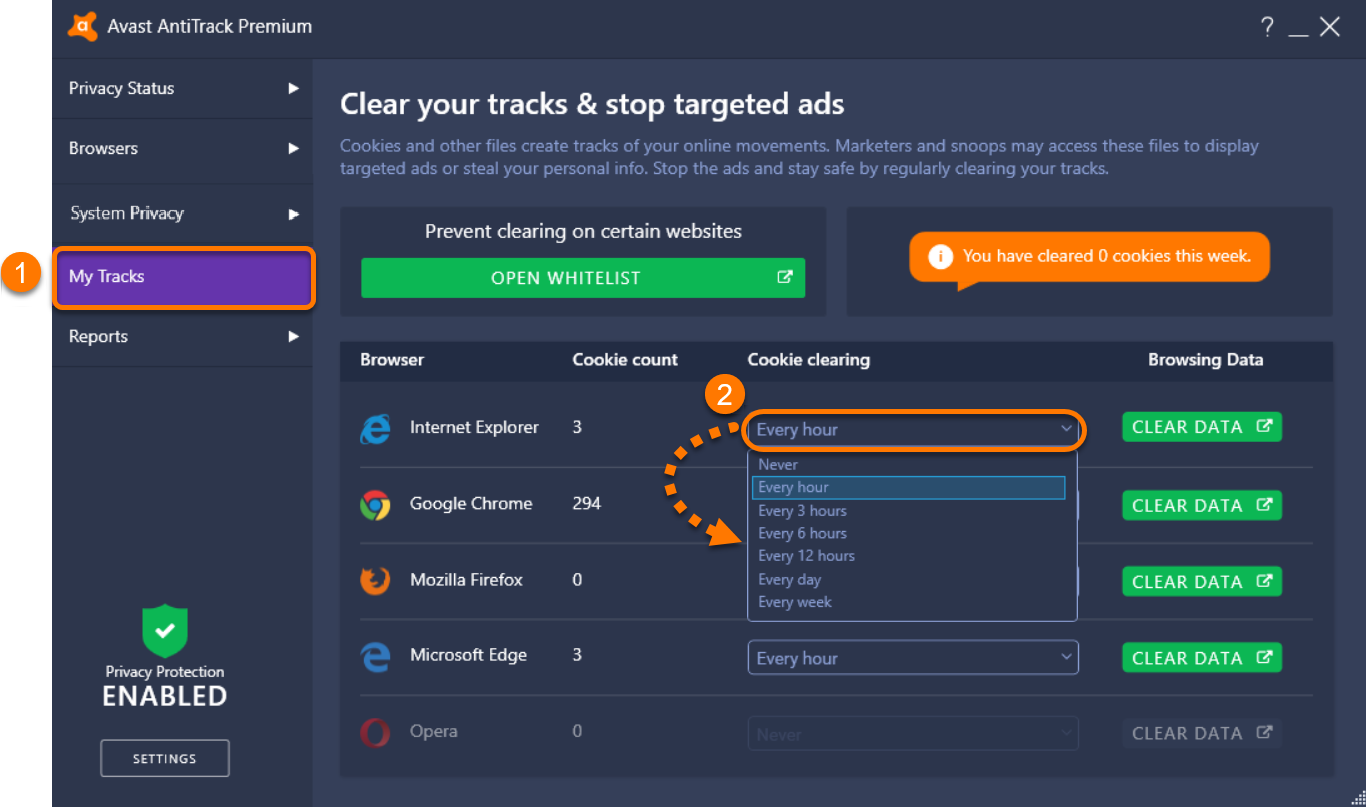
Each OS stores them in a different location. Research where the directory is located on your PC and review the files before deleting or keeping them.
How Do I Manage Cookies?
You can usually delete cookies from the Privacy or History area, available from the Settings or Options menu in the browser. In most browsers, the same menu can be reached through:
- Ctrl+Shift+Del keyboard shortcut for Windows or
- Command+Shift+Del if you're on a Mac.
To emphasize, the steps involved in deleting cookies can differ depending on what web browser we're talking about.
Implement a VPN System for an Added Layer of Protection
There are steps you can take on your local PC to minimize the impact of web cookies. In addition, use hide.me VPN to mask your computer's details. In doing that, you will supply a false IP address to the marketers that use cookies. One of the most concerning data points contained in a web cookie is the IP address of the user it belongs to. An IP address contains sensitive geographic information. They use this to pinpoint your exact location. By using cookies web site owners can even pull up your personal information via your internet service provider.
Use hide.me VPN and your true IP address will stay masked from the website you're communicating with. The website sees only the VPN server's IP. That is because all traffic goes through hide.me VPN servers. That way your IP stays hidden. This creates an effective diversion that prevents your geographic location being revealed to the website owner. Paired with the practices mentioned in the second section of this post, a VPN will create an airtight seal against the invasive monitoring by cookie owners.
Summary
In conclusion, most users don't realize the extent to which they are being tracked and monitored by web cookies. Addressing cookies is an effective way to limit the information you provide. But, there are many other methods to be vary of. These are outside the scope of this post. At last, utilize the recommendations in this post. Prevent cookies on your PC. In addition, use hide.me VPN to enjoy the peace of mind of your activity remaining private.
If you have any other concerns that need addressing, contact our Support team directly.
-->Important
Cookie 5 7 5 – Protect Your Online Privacy Screen
The improved Microsoft 365 security center is now available in public preview. This new experience brings Defender for Endpoint, Defender for Office 365, Microsoft 365 Defender, and more into the Microsoft 365 security center. Learn what's new. This topic might apply to both Microsoft Defender for Office 365 and Microsoft 365 Defender. Refer to the Applies To section and look for specific call-outs in this article where there might be differences.
Cookie 5 7 5 – Protect Your Online Privacy Screen Protector
Applies to
As an admin, you might have company requirements to restrict or control automatically forwarded messages to external recipients (recipients outside of your organization). Email forwarding can be a useful, but can also pose a security risk due to the potential disclosure of information. Attackers might use this information to attack your organization or partners.
The following types of automatic forwarding are available in Microsoft 365:
Users can configure Inbox rules to automatically forward messages to external senders (deliberately or as a result of a compromised account).
Admins can configure mailbox forwarding (also known as SMTP forwarding) to automatically forward messages to external recipients. The admin can choose whether to simply forward messages, or keep copies of forwarded messages in the mailbox.
You can use outbound spam filter policies to control automatic forwarding to external recipients. Three settings are available:
- Automatic: Automatic external forwarding is blocked. Internal automatic forwarding of messages will continue to work. This is the default setting.
- On: Automatic external forwarding is allowed and not restricted.
- Off: Automatic external forwarding is disabled and will result in a non-delivery report (also known as an NDR or bounce message) to the sender.
For instructions on how to configure these settings, see Configure outbound spam filtering in EOP.
Note
Disabling automatic forwarding disables any Inbox rules (users) or mailbox forwarding (admins) that redirect messages to external addresses.
Automatic forwarding of messages between internal users isn't affected by the settings in outbound spam filter policies.
You can see information about users that are automatically forwarding messages to external recipients in the Auto-forwarded messages report.
How the outbound spam filter policy settings work with other automatic email forwarding controls
As an admin, you might have already configured other controls to allow or block automatic email forwarding. For example:
Remote domains to allow or block automatic email forwarding to some or all external domains.
Conditions and actions in Exchange mail flow rules (also known as transport rules) to detect and block automatically forwarded messages to external recipients.

Each OS stores them in a different location. Research where the directory is located on your PC and review the files before deleting or keeping them.
How Do I Manage Cookies?
You can usually delete cookies from the Privacy or History area, available from the Settings or Options menu in the browser. In most browsers, the same menu can be reached through:
- Ctrl+Shift+Del keyboard shortcut for Windows or
- Command+Shift+Del if you're on a Mac.
To emphasize, the steps involved in deleting cookies can differ depending on what web browser we're talking about.
Implement a VPN System for an Added Layer of Protection
There are steps you can take on your local PC to minimize the impact of web cookies. In addition, use hide.me VPN to mask your computer's details. In doing that, you will supply a false IP address to the marketers that use cookies. One of the most concerning data points contained in a web cookie is the IP address of the user it belongs to. An IP address contains sensitive geographic information. They use this to pinpoint your exact location. By using cookies web site owners can even pull up your personal information via your internet service provider.
Use hide.me VPN and your true IP address will stay masked from the website you're communicating with. The website sees only the VPN server's IP. That is because all traffic goes through hide.me VPN servers. That way your IP stays hidden. This creates an effective diversion that prevents your geographic location being revealed to the website owner. Paired with the practices mentioned in the second section of this post, a VPN will create an airtight seal against the invasive monitoring by cookie owners.
Summary
In conclusion, most users don't realize the extent to which they are being tracked and monitored by web cookies. Addressing cookies is an effective way to limit the information you provide. But, there are many other methods to be vary of. These are outside the scope of this post. At last, utilize the recommendations in this post. Prevent cookies on your PC. In addition, use hide.me VPN to enjoy the peace of mind of your activity remaining private.
If you have any other concerns that need addressing, contact our Support team directly.
-->Important
Cookie 5 7 5 – Protect Your Online Privacy Screen
The improved Microsoft 365 security center is now available in public preview. This new experience brings Defender for Endpoint, Defender for Office 365, Microsoft 365 Defender, and more into the Microsoft 365 security center. Learn what's new. This topic might apply to both Microsoft Defender for Office 365 and Microsoft 365 Defender. Refer to the Applies To section and look for specific call-outs in this article where there might be differences.
Cookie 5 7 5 – Protect Your Online Privacy Screen Protector
Applies to
As an admin, you might have company requirements to restrict or control automatically forwarded messages to external recipients (recipients outside of your organization). Email forwarding can be a useful, but can also pose a security risk due to the potential disclosure of information. Attackers might use this information to attack your organization or partners.
The following types of automatic forwarding are available in Microsoft 365:
Users can configure Inbox rules to automatically forward messages to external senders (deliberately or as a result of a compromised account).
Admins can configure mailbox forwarding (also known as SMTP forwarding) to automatically forward messages to external recipients. The admin can choose whether to simply forward messages, or keep copies of forwarded messages in the mailbox.
You can use outbound spam filter policies to control automatic forwarding to external recipients. Three settings are available:
- Automatic: Automatic external forwarding is blocked. Internal automatic forwarding of messages will continue to work. This is the default setting.
- On: Automatic external forwarding is allowed and not restricted.
- Off: Automatic external forwarding is disabled and will result in a non-delivery report (also known as an NDR or bounce message) to the sender.
For instructions on how to configure these settings, see Configure outbound spam filtering in EOP.
Note
Disabling automatic forwarding disables any Inbox rules (users) or mailbox forwarding (admins) that redirect messages to external addresses.
Automatic forwarding of messages between internal users isn't affected by the settings in outbound spam filter policies.
You can see information about users that are automatically forwarding messages to external recipients in the Auto-forwarded messages report.
How the outbound spam filter policy settings work with other automatic email forwarding controls
As an admin, you might have already configured other controls to allow or block automatic email forwarding. For example:
Remote domains to allow or block automatic email forwarding to some or all external domains.
Conditions and actions in Exchange mail flow rules (also known as transport rules) to detect and block automatically forwarded messages to external recipients.
Remote domain settings and mail flow rules are independent of the settings in outbound spam filter policies. For example:
You allow automatic forwarding for a remote domain, but you block automatic forwarding in outbound spam filter policies. In this example, automatically forwarded messages are blocked.
You allow automatic forwarding in outbound spam filter policies, but you use mail flow rules or remote domain settings to block automatically forwarded email. In this example, the mail flow rules or remote domain settings will block automatically forwarded messages.
This feature independence allows you to (for example) allow automatic forwarding in outbound spam filter policies, but use remote domains to control the external domains that users can forward messages to.
Blocked email forwarding messages
When a message is detected as automatically forwarded, and the outbound spam filter policy blocks that activity, the message is returned to the sender in an NDR that contains the following information:
5.7.520 Access denied, Your organization does not allow external forwarding. Please contact your administrator for further assistance. AS(7555)

